Security Features in Modern Operating Systems: A Comparison
Modern operating systems are the first line of defense against digital threats, employing a range of security features to safeguard user data and system integrity. This blog post provides an overview of operating system security, detailing core security mechanisms found in Windows, macOS, and Linux. It compares their security models, highlighting the strengths and weaknesses of each. Furthermore, the article outlines practical steps users can take to enhance their system’s security, going beyond the built-in features for comprehensive protection.
Understanding Operating System Security: An Overview
Operating system (OS) security is a critical aspect of modern computing, safeguarding systems and data from a wide range of threats. It encompasses the strategies and techniques implemented to ensure the confidentiality, integrity, and availability of an OS and its hosted resources. A robust OS security framework is the foundation upon which all other security measures are built, protecting against malware, unauthorized access, and various cyber-attacks. Understanding the core principles and mechanisms of OS security is essential for anyone involved in IT management, software development, or cybersecurity.
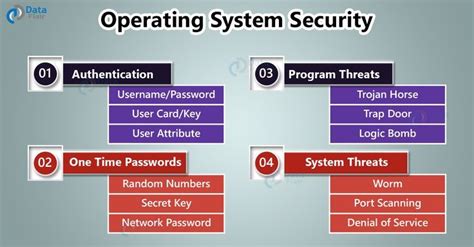
At its core, OS security aims to control access to system resources and prevent unauthorized actions. This involves several layers of defense, including authentication, authorization, and auditing. Authentication verifies the identity of users and processes, ensuring that only legitimate entities gain access. Authorization determines what actions authenticated users and processes are allowed to perform. Auditing tracks system activity, providing a record of events that can be used to detect and investigate security incidents. These mechanisms work together to enforce security policies and protect sensitive data.
Key Aspects of OS Security:
- Authentication: Verifying user and process identities.
- Authorization: Defining access rights and permissions.
- Access Control: Restricting access to resources based on privileges.
- Memory Protection: Preventing processes from interfering with each other’s memory.
- File System Security: Protecting files and directories from unauthorized access.
- Security Auditing: Tracking system events and activities for security analysis.
The effectiveness of OS security features depends on a combination of well-designed security mechanisms and diligent administration. Regular security updates and patches are crucial for addressing vulnerabilities and mitigating potential risks. Additionally, user awareness and adherence to security best practices play a significant role in maintaining a secure computing environment. As cyber threats continue to evolve, a proactive and comprehensive approach to OS security is essential for protecting valuable assets and ensuring business continuity.
Security Features Implemented In Modern OS
Modern operating systems are built with a range of security features designed to protect against various threats. These features work together to create a layered security approach, safeguarding user data and system integrity. Understanding these core components is crucial for appreciating how operating systems defend against malware, unauthorized access, and data breaches. The evolution of these features reflects the ever-changing landscape of cybersecurity threats.
One fundamental aspect of OS security is controlling access to system resources. This involves verifying user identities, managing permissions, and enforcing security policies. Access control mechanisms ensure that only authorized users can access sensitive data and perform critical operations. These mechanisms are crucial for preventing unauthorized modification, deletion, or disclosure of information. Strong access control is a cornerstone of any secure operating system, preventing malicious actors from gaining a foothold.
Access Control Mechanisms
Access control mechanisms are the gatekeepers of the operating system, determining who can access what. These mechanisms range from simple username/password authentication to more advanced biometric and multi-factor authentication methods. The goal is to ensure that only legitimate users gain access to the system and its resources.
- User Authentication: Verifying the identity of users through passwords, biometrics, or multi-factor authentication.
- Access Control Lists (ACLs): Defining permissions for specific users or groups on files and directories.
- Role-Based Access Control (RBAC): Assigning roles to users and granting permissions based on those roles.
- Least Privilege: Granting users only the minimum level of access necessary to perform their tasks.
- Mandatory Access Control (MAC): Enforcing strict access control policies based on security labels.
Memory management techniques play a vital role in preventing security vulnerabilities such as buffer overflows and memory leaks. Modern operating systems employ various memory protection mechanisms to isolate processes and prevent them from interfering with each other. These techniques help to ensure the stability and security of the system by preventing malicious code from corrupting memory.
Memory Management Techniques
Effective memory management is crucial for preventing exploits that target memory vulnerabilities. Techniques like address space layout randomization (ASLR) and data execution prevention (DEP) make it more difficult for attackers to inject and execute malicious code in memory. These features are essential for mitigating common attack vectors and enhancing overall system security.
Below is a comparison of memory management features in popular operating systems.
| Operating System | Address Space Layout Randomization (ASLR) | Data Execution Prevention (DEP) | Memory Isolation |
|---|---|---|---|
| Windows | Yes | Yes | Process-based |
| MacOS | Yes | Yes | Process-based |
| Linux | Yes | Yes | Process-based, Namespaces, cgroups |
| Android | Yes | Yes | Process-based, Sandboxing |
Encryption is a cornerstone of data protection in modern operating systems. Encryption mechanisms protect data both at rest and in transit, ensuring that sensitive information remains confidential even if it is intercepted or accessed by unauthorized individuals. Encryption keys are carefully managed and protected to prevent unauthorized decryption.
Encryption and Data Protection
Modern operating systems provide robust encryption capabilities to protect data from unauthorized access. Full disk encryption, file-level encryption, and secure communication protocols are essential tools for maintaining data confidentiality and integrity. By encrypting sensitive data, organizations can mitigate the risk of data breaches and comply with regulatory requirements.
In addition to these core features, modern operating systems incorporate various other security mechanisms, such as firewalls, intrusion detection systems, and security auditing tools. These features work together to provide a comprehensive defense against a wide range of threats. Staying informed about these security features and keeping them up-to-date is essential for maintaining a secure computing environment.
Okay, I will create a content section for your blog post, focusing on comparing the security models of Windows, macOS, and Linux. Here is the content: html
Comparing Security Models: Windows, MacOS, And Linux
When evaluating operating systems, understanding their security models is crucial. Each OS—Windows, macOS, and Linux—implements distinct approaches to protect against threats, manage user privileges, and ensure system integrity. These security features are deeply ingrained in their architecture, influencing how they handle everything from malware to user authentication.
- Windows: Known for its wide software compatibility, Windows employs a robust access control list (ACL) system and User Account Control (UAC) to manage permissions.
- macOS: Leveraging a Unix-based foundation, macOS emphasizes sandboxing, code signing, and System Integrity Protection (SIP) to secure the OS and applications.
- Linux: With its open-source nature, Linux benefits from community-driven security audits, a flexible permission system, and a variety of security-focused distributions.
Windows, developed by Microsoft, uses a comprehensive security architecture built around the NT kernel. Key components include its Access Control Model, which specifies permissions for users and groups, and the Windows Defender Antivirus, a built-in solution that protects against malware. User Account Control (UAC) is another critical feature, prompting users for permission before making changes that could affect system stability or security. Despite these measures, Windows has historically been a larger target for malware due to its widespread use, necessitating constant updates and vigilance.
| Feature | Windows | MacOS | Linux |
|---|---|---|---|
| Access Control | ACL, UAC | Sandboxing, SIP | Permissions, SELinux |
| Kernel Security | NT Kernel | XNU Kernel | Linux Kernel |
| Malware Protection | Windows Defender | XProtect | Varies (ClamAV, etc.) |
| Open Source | No | Partially | Yes |
macOS, by Apple, integrates security deeply into its Unix-based core. Features like System Integrity Protection (SIP) prevent unauthorized modification of system files, even by users with root privileges. Sandboxing restricts applications to specific resources, limiting potential damage from compromised software. Furthermore, Apple’s code signing requirements ensure that only trusted software can run, reducing the risk of malware. While macOS has fewer reported vulnerabilities than Windows, its increasing popularity makes it a more attractive target for cyberattacks.
Linux, characterized by its open-source nature, relies on a community-vetted kernel and a flexible permission system for security. Distributions like Ubuntu, Fedora, and Debian offer various security configurations and tools, including firewalls (iptables, nftables) and intrusion detection systems. Security-Enhanced Linux (SELinux) provides mandatory access control, adding an extra layer of protection. The open-source model allows for continuous auditing and rapid patching of vulnerabilities, making Linux a robust choice for security-conscious users and servers. The command line can be used to fine-tune settings that can increase protection.
Enhancing Your System’s Security: Practical Steps
Securing your operating system is an ongoing process that requires diligence and a proactive approach. Understanding the available tools and techniques is crucial, but implementing them effectively is where you truly enhance your system’s security features. This section outlines practical steps you can take to bolster your defenses against potential threats, ensuring a safer and more secure computing environment.
One of the most impactful measures you can take is regularly updating your operating system and applications. Software updates often include critical security patches that address newly discovered vulnerabilities. Ignoring these updates leaves your system exposed to known exploits. Furthermore, enabling automatic updates can help ensure you’re always running the latest, most secure versions.
| Tool/Technique | Description | Benefits |
|---|---|---|
| Firewall | Monitors and controls network traffic based on predefined rules. | Blocks unauthorized access and malicious connections. |
| Antivirus Software | Detects, prevents, and removes malware. | Protects against viruses, worms, Trojans, and other malicious software. |
| Two-Factor Authentication (2FA) | Requires a second verification method in addition to a password. | Adds an extra layer of security, making it harder for attackers to gain access. |
| Regular Backups | Creating copies of important data and storing them separately. | Ensures data recovery in case of system failure, ransomware attacks, or other disasters. |
Beyond software updates, consider implementing stronger authentication methods. Passwords alone are often insufficient, especially if they are weak or reused across multiple accounts. Two-factor authentication (2FA) adds an extra layer of security by requiring a second verification method, such as a code sent to your phone. Using a password manager can also help you create and manage strong, unique passwords for all your accounts.
Another essential aspect of enhancing your system’s security features is educating yourself and your users about common threats and attack vectors. Phishing scams, social engineering, and malicious websites are common ways attackers attempt to compromise systems. By staying informed and practicing safe online habits, you can significantly reduce your risk of falling victim to these attacks.
- Actionable Steps to Improve Security:
- Enable automatic updates for your operating system and applications.
- Implement two-factor authentication (2FA) on all supported accounts.
- Use a strong, unique password for each account.
- Install and regularly update antivirus software.
- Enable your firewall and configure it to block unauthorized access.
- Regularly back up your important data to a secure, offsite location.
Finally, regularly review your system’s security settings and audit logs. This will help you identify potential vulnerabilities and detect any suspicious activity. Consider using security auditing tools to automate this process and generate reports that highlight areas for improvement. Remember, maintaining a secure system is an ongoing effort that requires constant vigilance and adaptation to new threats.